Lilliput-AE Specifications
Authenticated Encryption Modes
Lilliput-AE is composed of two authenticated encryption modes:
- Lilliput-I
- Lilliput-II
Lilliput-I is a nonce-respecting mode ΘCB3
Lilliput-II is a nonce-misuse resistant mode SCT-2
Primary member: Lilliput-II-128
| Name | k | t | n | |N| | τ |
|---|---|---|---|---|---|
| Lilliput-I-128 | 128 | 192 | 128 | 120 | 128 |
| Lilliput-I-192 | 192 | 192 | 128 | 120 | 128 |
| Lilliput-I-256 | 256 | 192 | 128 | 120 | 128 |
| Lilliput-II-128 | 128 | 128 | 128 | 120 | 128 |
| Lilliput-II-192 | 192 | 128 | 128 | 120 | 128 |
| Lilliput-II-256 | 256 | 128 | 128 | 120 | 128 |
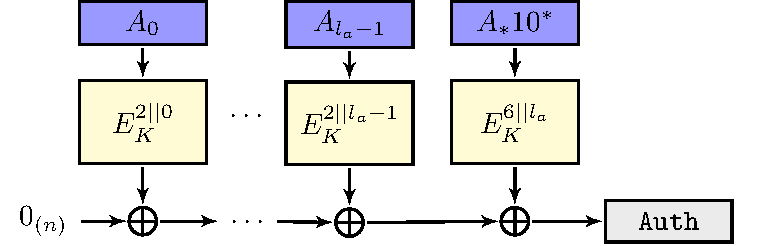
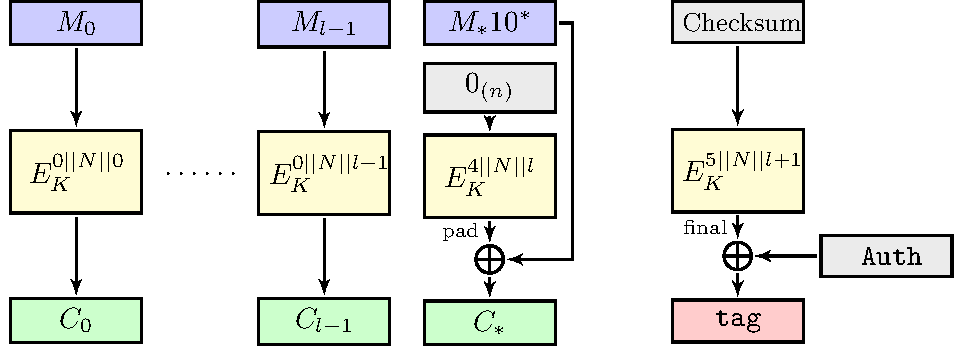
Lilliput-I: nonce-respecting mode ΘCB3
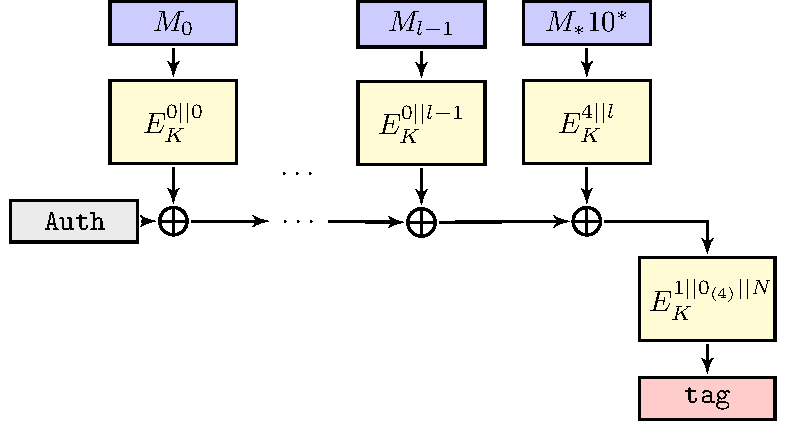
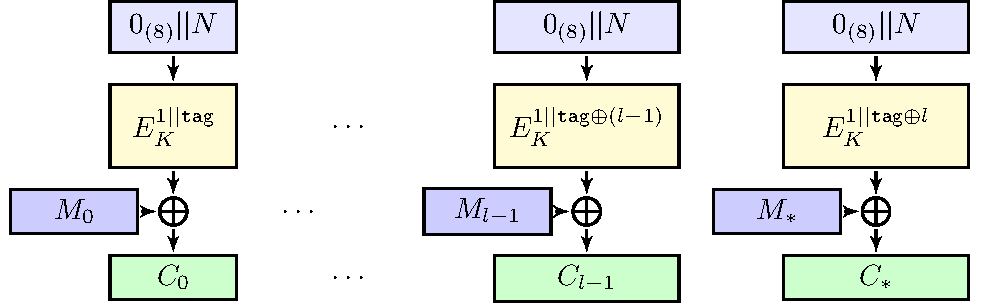
Lilliput-II: nonce-misuse resistant mode SCT-2

The Tweakable Block Cipher Lilliput-TBC
based on the block cipher Lilliput
Lilliput-TBC is composed of 6 variants
| Name | k | t | Nb of rounds r | |
|---|---|---|---|---|
| Lilliput-TBC-I-128 | 128 | 192 | 32 | |
| Lilliput-TBC-I-192 | 192 | 192 | 36 | |
| Lilliput-TBC-I-256 | 256 | 192 | 42 | |
| Lilliput-TBC-II-128 | 128 | 128 | 32 | |
| Lilliput-TBC-II-192 | 192 | 128 | 36 | |
| Lilliput-TBC-II-256 | 256 | 128 | 42 |
Lilliput-TBC Encryption process (decryption analogous to encryption but uses the inverse block permutation π−1 and the subkeys in the reverse order):
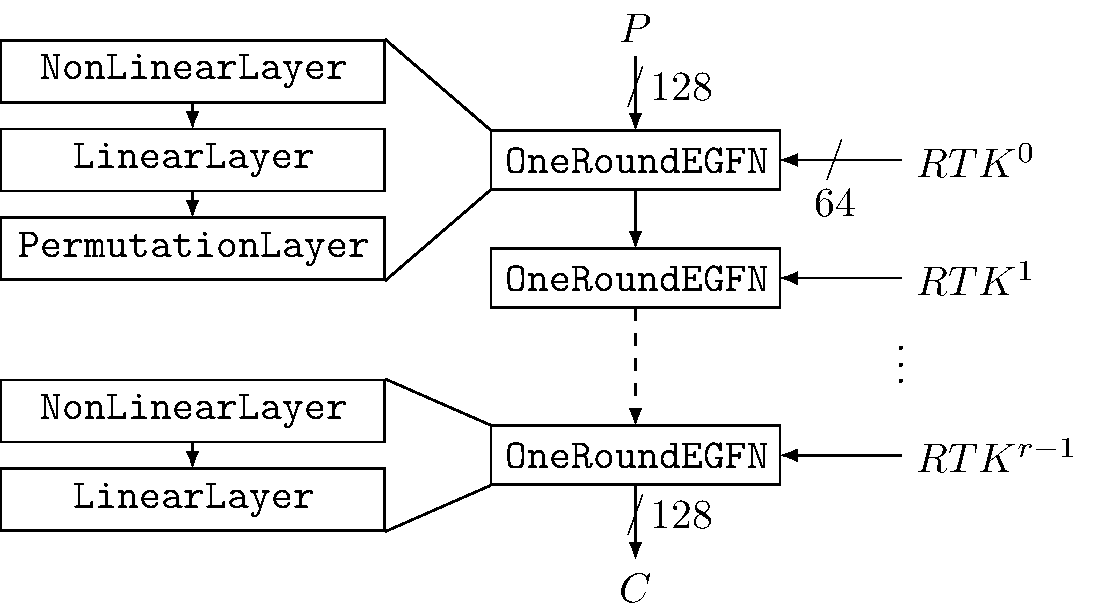
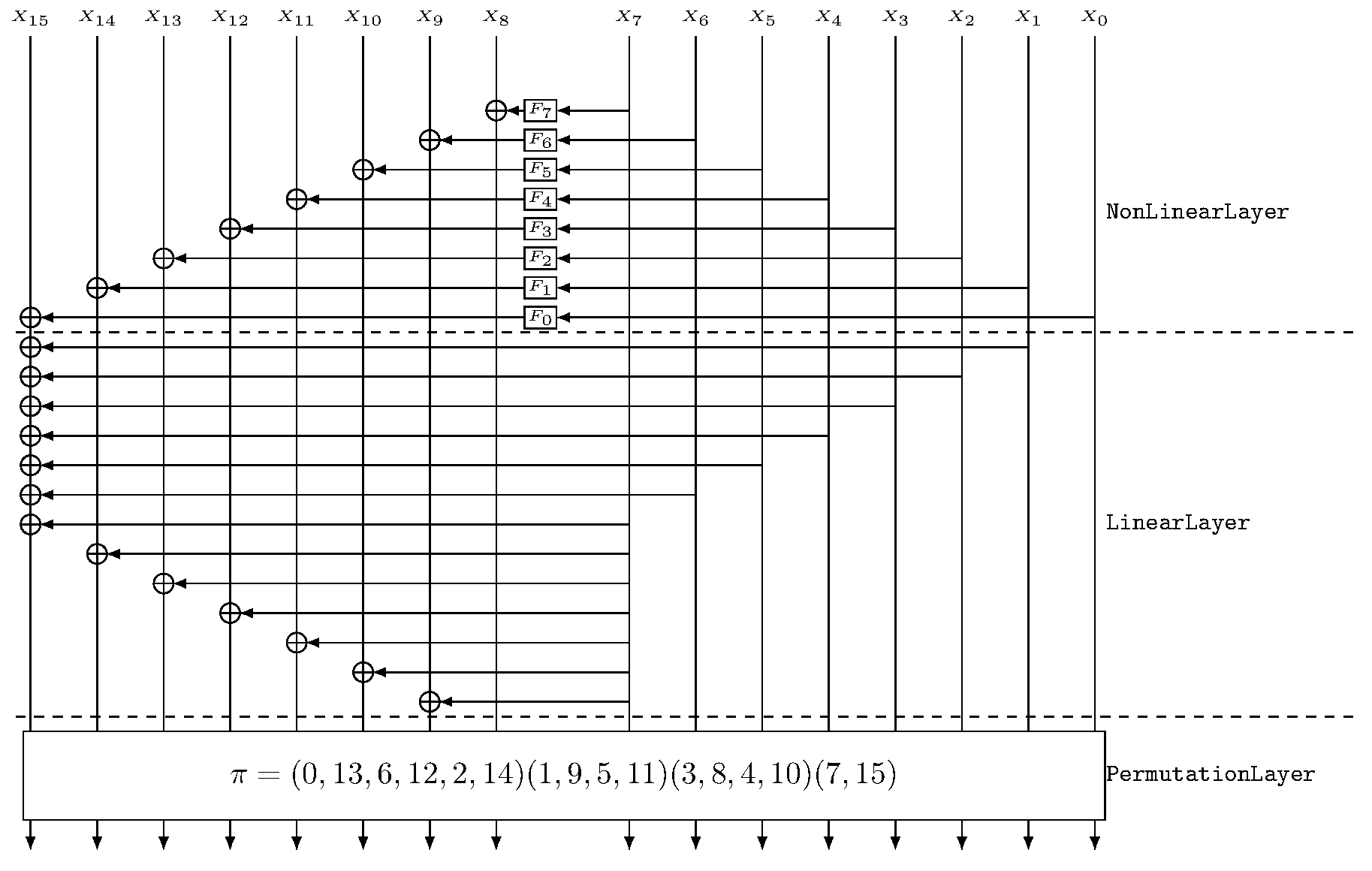
Lilliput-TBC: the round function
The round function OneRoundEGFN based on a EGFN used in Lilliput-TBC with
Fj = S(Xj ⊕ RTKji):
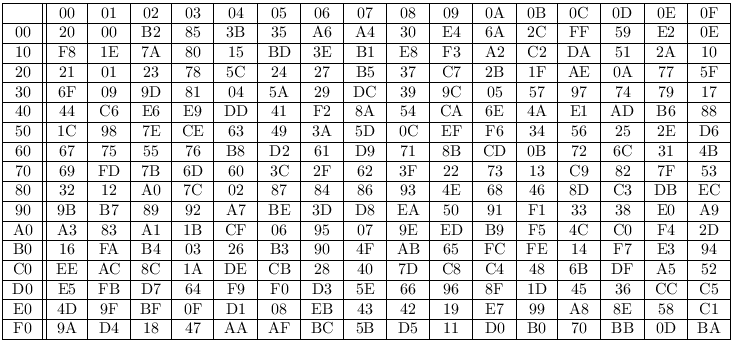
Lilliput-TBC: the S-box
The S-box in hexadecimal notation:
Chosen for its good cryptographic properties (resistance against linear/differential cryptanalysis, high algebraic degree, etc.)
Based on a 3-round Feistel scheme with two APN functions and a 4-bit S-box in the middle round
Chosen for its low cost in terms of hardware implementation and of side-channel resistance
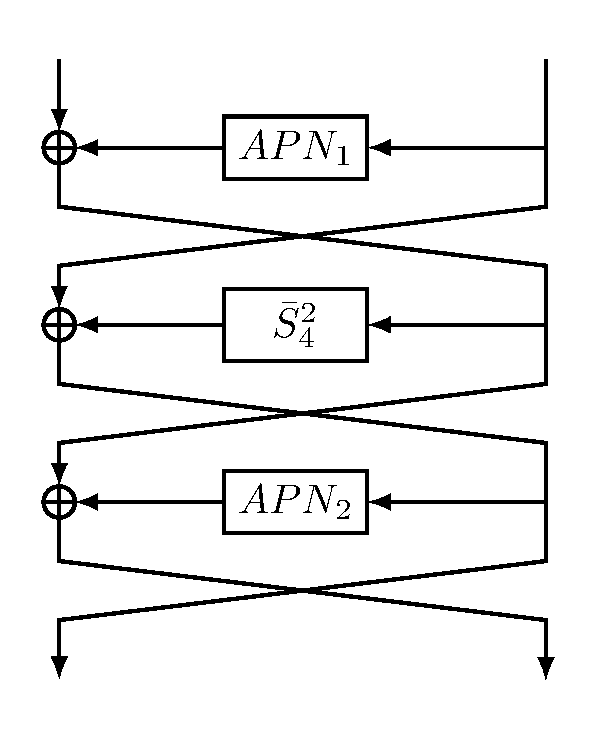
The 4-bit S-box used in the 3-round Feistel Scheme composed of two applications of the same quadratic function:
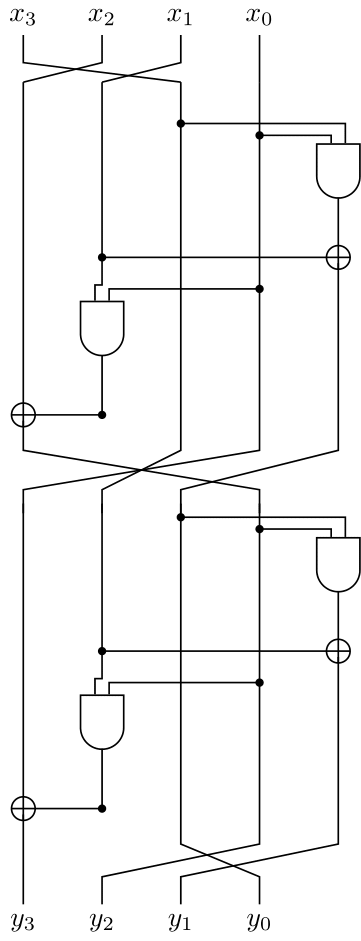
Tweakey Schedule
An adapted version of the TWEAKEY framework: the key and the tweak inputs are handled almost the same way
The tweakey schedule produces the 64-bit subtweakeys RTK0 to RTKr − 1 from the master key K and the tweak T divided into p = (t + k)/64 lanes that we denote TKji
| Name | k | t | p | r | |
|---|---|---|---|---|---|
| Lilliput-TBC-I-128 | 128 | 192 | 5 | 32 | |
| Lilliput-TBC-I-192 | 192 | 192 | 6 | 36 | |
| Lilliput-TBC-I-256 | 256 | 192 | 7 | 42 | |
| Lilliput-TBC-II-128 | 128 | 128 | 4 | 32 | |
| Lilliput-TBC-II-192 | 192 | 128 | 5 | 36 | |
| Lilliput-TBC-II-256 | 256 | 128 | 6 | 42 |
![The tweakey schedule. *f* represents the round function
`OneRoundEGFN`. \[tkv2\]](../img/tweakeyv2.png)
- the α0, ⋯, α*p* − 1 has been chosen as produced by word-ring LFSRs to improve software and hardware performances
Security Analysis Summary
| STKM | RTKM | Nb rounds | Security margin | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Diff. | Lin. | Struct. | Diff. | Lin. | RTKB | Struct. | ||||
| LILLIPUT-TBC-I-128 | 21 | 24 | 18 | 27 | 24 | 28 | 23 | 32 | 4 | |
| LILLIPUT-TBC-I-192 | 25 | 31 | 18 | 32 | 31 | 32 | 24 | 36 | 4 | |
| LILLIPUT-TBC-I-256 | 32 | 38 | 18 | 40 | 38 | 36 | 25 | 42 | 2 | |
| LILLIPUT-TBC-II-128 | 21 | 24 | 18 | 26 | 24 | 26 | 22 | 32 | 6 | |
| LILLIPUT-TBC-II-192 | 25 | 31 | 18 | 31 | 31 | 30 | 23 | 36 | 5 | |
| LILLIPUT-TBC-II-256 | 32 | 38 | 18 | 39 | 38 | 34 | 24 | 42 | 3 | |